Looks like a new round of phishing attacks are well underway, targeting Facebook users. There are a few going around, and they seem to work slightly differently (although same principle) to the previous round of virus/phishing attacks from last year, featuring the Bolivar23.exe virus and the Koobface virus.
These phishing links ask the users to put in their Facebook Login credentials. Once the mistake of entering Facebook credentials is done, the attack changes the password and sends same phishing link to victim’s contacts. This attack doesn’t install malware and is presumed to be in stage of collecting user credentials for a larger damage in the future.
Please note – for the Mac/Linux users, the fact that it doesn’t install malware means YOU are also vulnerable. Instead of using virus installations to send out these messages, they are are relying simply on the fact that people don’t always pay attention, and have conditioned responses to login prompts. That means everyone on every operating system and every browser are at risk.
Don’t “Look at This”
I’ve received several Facebook messages from friends with either no subject to the message at all, or the subject “Look at this”. The messages contain a note telling me to visit one of a few phishing sites, and the url has been obfuscated so that it’s not clickable in the Facebook message.
The domains I’ve seen so far:
- goldbase.be
- greenbuddy.be
- silvertag.be
- picoband.be
- nudz.ru
- simplemart.be
ALL of the above domains are phishing websites, and you should not under any circumstances click on them. It seems that Facebook has already deleted the harmful messages from my actual Facebook account inbox, but a copy was already sent to me via email notification, so be mindful of what you’re clicking on.
So far, Facebook has been very good about being proactive to protect users, by deleting these phishing scam messages from user accounts, and perhaps even more importantly, notifying Markmonitor. If you’re using FireFox, IE8 or other modern browser that tries to warn you against phishing sites, you should be presented with a big fat warning if you do accidentally click on the urls – however new domain names seem to keep popping up, so you should ALWAYS remember to check the actual url bar to make sure whatever site you’re logging into is the real thing.
Fbaction.Net
Another recent phishing attempt is one that sends messages from an infected account that asks that you click on a url that looks an awful lot like a real Facebook url, but really redirects back to a website called fbaction.net, which is a phishing site. A message would look something like this:
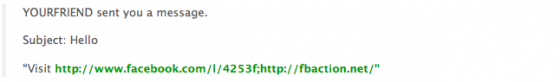
This url redirects to fbaction.net, and prompts the user to enter their Facebook credentials. The page looks exactly like a standard Facebook login, but the url is clearly not Facebook:
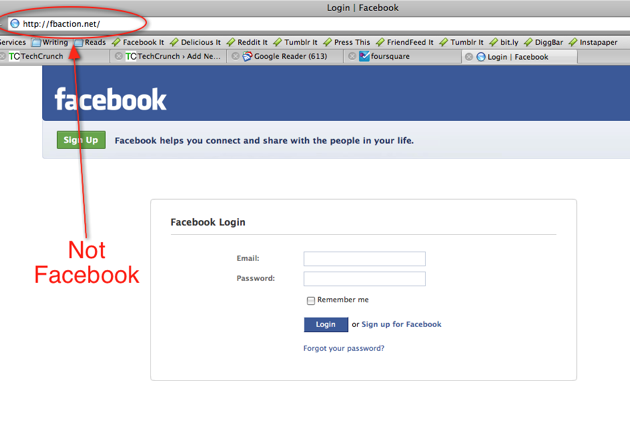
According to an excellent TechCrunch article, Facebook has already taken steps to protect users from falling victim to this scam. Facebook told them:
We are aware of this phishing domain and have already begun to take action. Specifically, we have passed the domain on to Markmonitor who pushes the domain to the browsers for blacklisting. They will also actively try to disable the site at the server/domain level for people who don’t have updated browsers. Our user operations team has blocked the domain from being shared on Facebook and is removing the content retroactively from any messages. They will also be resetting passwords of senders to remove access from an attacker. We’re also reaching out to the ISPs to get information and will attempt to build a civil and/or criminal case against the owners.
This behavior is very similar to the recent attacks tricking users to go to domains like apreps.at (more at TechCrunch), and 151.im (more at TechCrunch).
Keeping yourself safe
One might wonder what the end goal is for collecting millions of Facebook user logins – however many people use the same login credentials for many of their online accounts – even email accounts – which means a malicious website that has obtained the login for a user’s Facebook account could theoretically obtain access to any online account the user has that uses a relatively standard “I forgot my password” emailed password reminder system.
At the risk of overstating the obvious, this means that if a user uses the same login credentials for a social network and for anything else, if they become a victim in one of these phishing attempts, their email, online financial accounts and banking accounts, and so on are vulnerable to being hacked. Plus, if you use Facebook Connect to access any websites, once your Facebook account has been compromised, the malicious sites will have access to those websites under your account as well.
- Always check the url of a site prompting you for a login. Always. Every time. No matter how legit it looks.
- Always use unique passwords for every single website you have an account with. Programs like 1Password for Mac make this very easy to do, generating unique passwords for every sign-up, and storing them in the Mac OSX keychain. If you’re on a PC, consider KeePass or Roboform.
- Switch over or upgrade to a browser (like Firefox, IE8, etc) that supports warning users when they are about to enter a site known for phishing activity.
- Don’t get cocky. The people I have seen fall prey to these phishing attempts are not noobs, and not the type who blindly click on anything. These are reasonably tech savvy people who have become less careful than they should be.