A new scam has come to our attention, one that’s a new take on an old trick in Facebook. Scammers are adding users as page administrators on a page that’s got a poisoned IFRAME set as the default tab.
So the user gets a notification “John Smith has made you an administrator of XYZ page”. The user clicks on the page to see what they’ve just been made an admin of, and the poisoned default page tab kicks on, busting them out of the Facebook site and into a standalone page offering promises of free iPads and various other too-good-to-be-true freebies.
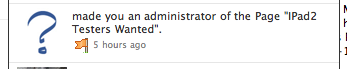
In this particular case, the scammers were using the extremely popular – and from what I can tell, legitimate – application Static HTML IFRAME, which simply allows people to create their own IFRAME tabs to add to their Facebook page without the hassle of creating their own application, hosting content, etc.
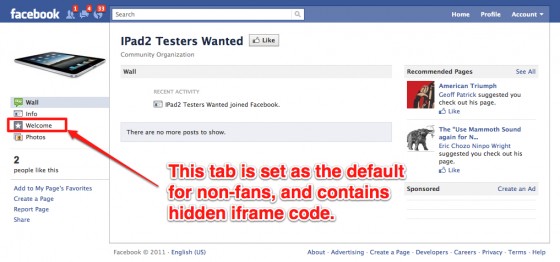
The IFRAME page that loads in the Facebook page points to s3.amazonaws.com/statichtmlplus/page/160281910702810.html – so it seems that the Static HTML IFRAME app just saves the content that their users add to their custom IFRAMEs into a static HTML file and serve it accordingly.
In the case of this scam, the IFRAME page hosted by the Static HTML IFRAME app contains another, hidden IFRAME inside of it that forces the browser to redirect to the scam website.
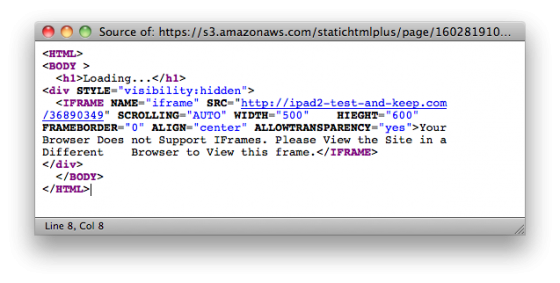
This is a combination of social engineering (taking advantage of the fact that the new administrator will obviously want to know what it is they’ve been made an admin of, thus getting them to look at a page they would otherwise never have found or cared about), and very basic technical jiggery pokery to bust out of the frames and take the unsuspecting admin to a third-party site.
The third party site in this case was a survey/iPad 2 giveaway scam (ipad2-test-and-keep.com), but this method could just as easily be used to serve malware or phishing pages.
Imagine how easily this would flow if if the frame-buster page instead took the user to a page that looks just like the Facebook login page. They think they’ve somehow been logged out, they fill in the login form to log back in, and now the bad guys have their Facebook credentials – which statistically are likely to be the same credentials they use for banking and other things.
The IP address of the scam site the IFRAME sends the user to, 92.241.169.80, tracks back to a Russian web hosting company, 2×4.ru.
We’ve already reported this scam page to Facebook using the normal routes and through the Preferred Developer Consultant avenues, but I’d be willing to bet we’re going to start to see a lot more of this kind of thing because it’s incredibly effective and very simple to execute.
Thanks to @uberbrady for seeing this for what it was when it happened to him, and bringing it to our attention.
Don’t forget to “like” our special Social Media Scam Alert page on Facebook and follow @scamdb on Twitter for more updates like this.